
MBUX, Mercedes-Benz User Experience is the infotainment system in Mercedes-Benz cockpits. Mercedes-Benz first introduced MBUX in the new A-Class back in 2018, and is adopting MBUX in their entire vehicle line-up, including Mercedes-Benz E-Class, GLE, GLS, EQC, etc.
In this research, we have conducted an in-depth and comprehensive analysis of both hardware and software of MBUX. We gathered technical materials and set up a test environment, analyzed the attack surfaces and performed security tests.
Modern infotainment system is much more powerful, complex and secure than before, so is MBUX from Mercedes-Benz. We haven’t seen any public material that gives a comprehensive security analysis of a modern infotainment system. So a broader security assessment is needed in this research, instead of a single security penetration event. We have explored the attack surfaces exhaustively including components such as the radio.
In our research, we found various security issues on MBUX and successfully exploited some attack surfaces on the head unit and T-Box. We have gained first physical access and subsequently remote access to the main infotainment ECU: the head unit. This enabled us to perform certain vehicle functions remotely (i.e. change internal lighting colors, display images on infotainment screen). We demonstrated how to compromise an internal chip on T-Box, which was proved by sending arbitrary CAN messages from a debug version T-Box.
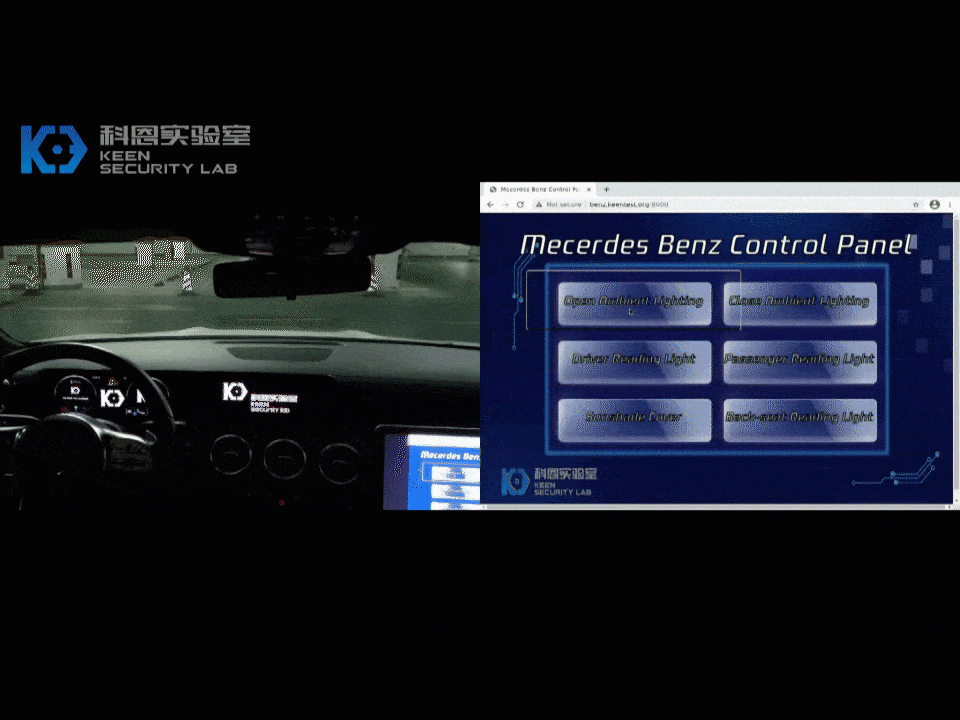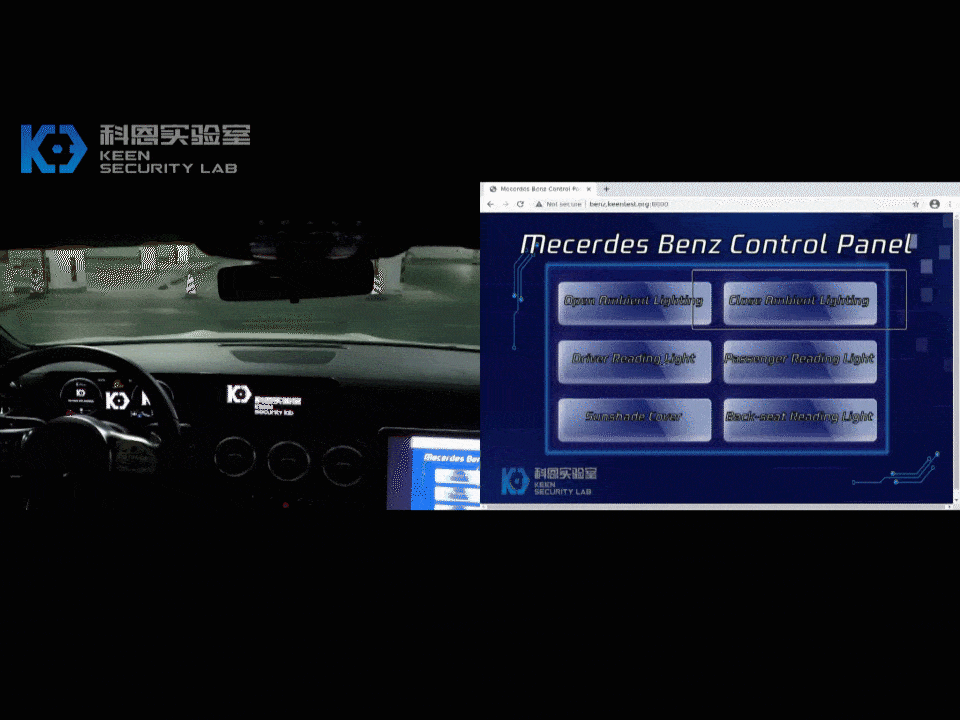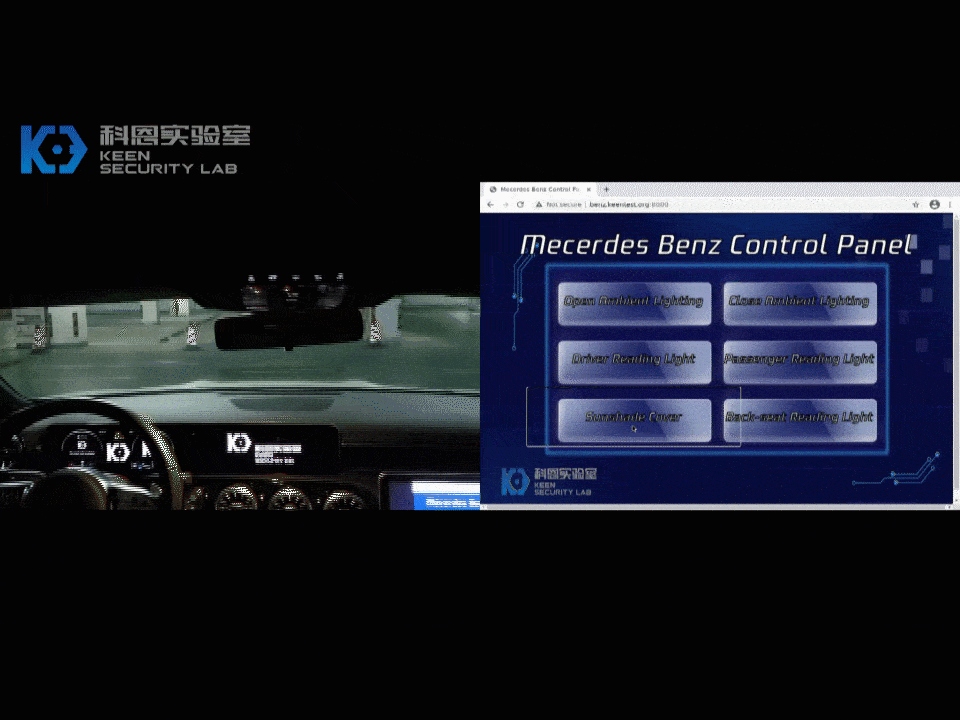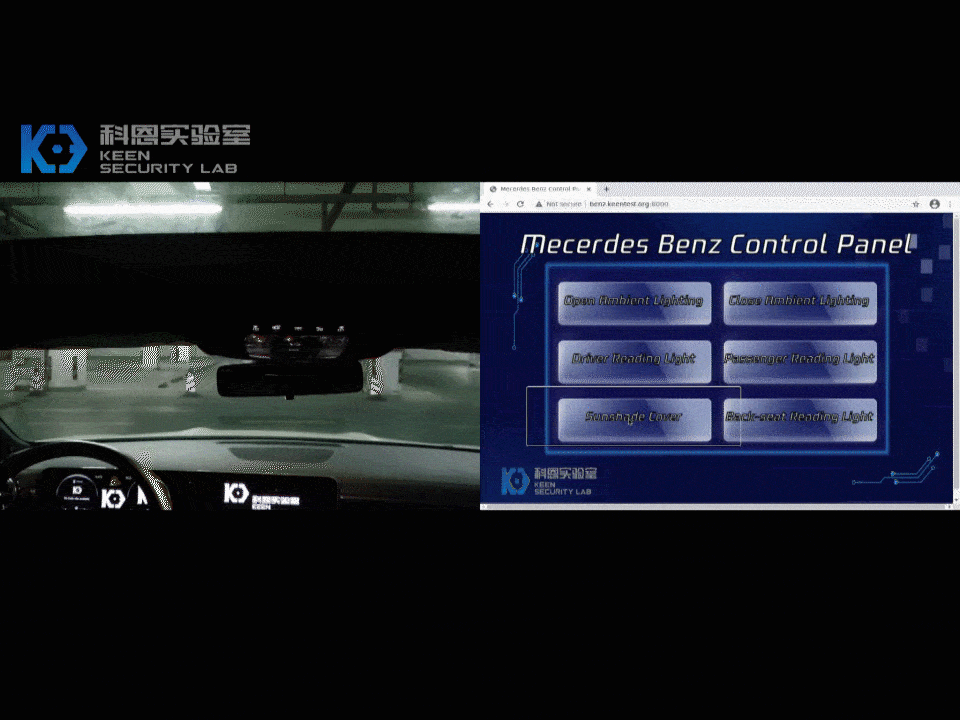
Following the global industry practice on “responsible disclosure” of product security vulnerabilities, we have reported the technical details of all the vulnerabilities discovered in this research to Daimler. The discovered vulnerabilities have been immediately confirmed by their security team.
Keen Lab appreciates the prompt response and proactive attitude of Daimler, on responding our vulnerability report and for taking direct action to fix the issues efficiently. Both companies collaborate closely and highly efficient.
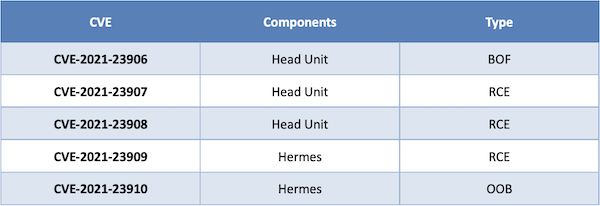
Issued CVEs:
Disclosure Timeline
March 2020: Keen Lab kicked off the Mercedes-Benz research project internally.
November 2020: Keen Lab proved all the vulnerability findings and attack chains in an experimental environment.
21st December 2020: First Email from Keen Lab to Daimler
24th December 2020: Keen Lab reported all the research findings to Daimler security team in a secure way.
7th January 2021: First clarification Call between Keen Lab and Daimler
15th January 2021: Daimler security team confirmed all the vulnerabilities reported by Keen Lab. Some fixes for these vulnerabilities were already available and in rollout.
21th January 2021: CVEs requested by Daimler security team.
30th January 2021: Daimler security team confirmed and started the rollout for the new fixes.
February/March 2021: Preparation of the joint report publication.
May 2021: This summary report has been released to public.
Response from Daimler
Please refer the following link for the press release from Daimler:
https://media.daimler.com/marsMediaSite/ko/en/49946866
Daimler security team highly appreciate Keen Lab’s profound know-how, expertise and its excellent work in the Mercedes-Benz research project, Daniel Eitler (CISO of Daimler) and Adi Ofek (the CarIT Security Mandate in Mercedes-Benz Cars) award Keen Lab the signed thank you letter.

Technical Research Report
Please refer the following link to know more about our research:
Mercedes-Benz MBUX Security Research Report.pdf
